Bedroom Set With Hidden Compartments
![]()
By , Contributing Writer, Computerworld |
Decoding Microsoft Defender's hidden settings
Though many Windows 10 users opt for third-party antivirus protection, those who use Microsoft Defender may not be getting all of the protection they could. Here's how to check your settings and what to change.
![A hand reaches to activate controls marked with gear icons [ process / update / fix / automate ]](https://images.idgesg.net/images/article/2020/08/hand_reaches_to_activate_controls_with_gear_icons_process_development_update_fix_automate_by_putilich_gettyimages-1220461550_2400x1600-100854509-large.jpg?auto=webp&quality=85,70)
Ask someone what antivirus software they use and you'll probably get a near-religious argument about which one they have installed. Antivirus choices are often about what we trust — or don't — on our operating system. I've seen some Windows users indicate they would rather have a third-party vendor watch over and protect their systems. Others, like me, view antivirus software as less important these days; it matters more that your antivirus vendor can handle windows updating properly and won't cause issues.
Still others rely on Microsoft Defender. It's been around in one form or another since Windows XP.
Defender recently had a zero-day issue that was silently fixed. As a result, I instructed many users to check which version of Defender they have installed. (To check: click on Start, then on Settings, then on Update and security, then on Windows Security, then Open windows security. Now, look for the gear (settings) and select About.
There are four lines of information here. The first gives you the Antimalware Client Version number. The second gives you the Engine version. The third gives you the antivirus version number. And the final number is the Antispyware version number. But what does it mean when Defender says its Engine version, Antivirus version and antispyware version is 0.0.0.0? It may mean that you have a third-party antivirus installed; it's taking over for Defender, which is thus properly shut off. Some people thought their "on demand" antivirus vendor was merely a scan-only tool, with Defender still the main antivirus tool. But if the third-party scanning tool is seen as a real-time antivirus, it will be the operative software on your system.
Defender involves more than just checking bad files and downloads. It offers a variety of settings most users don't check on a regular basis — or even know about. Some are exposed in the GUI. Others rely on third-party developers to deliver additional guidance and understanding. One such option is the ConfigureDefender tool on the GitHub download site. (ConfigureDefender exposes all of the settings you can use via PowerShell or the registry.)
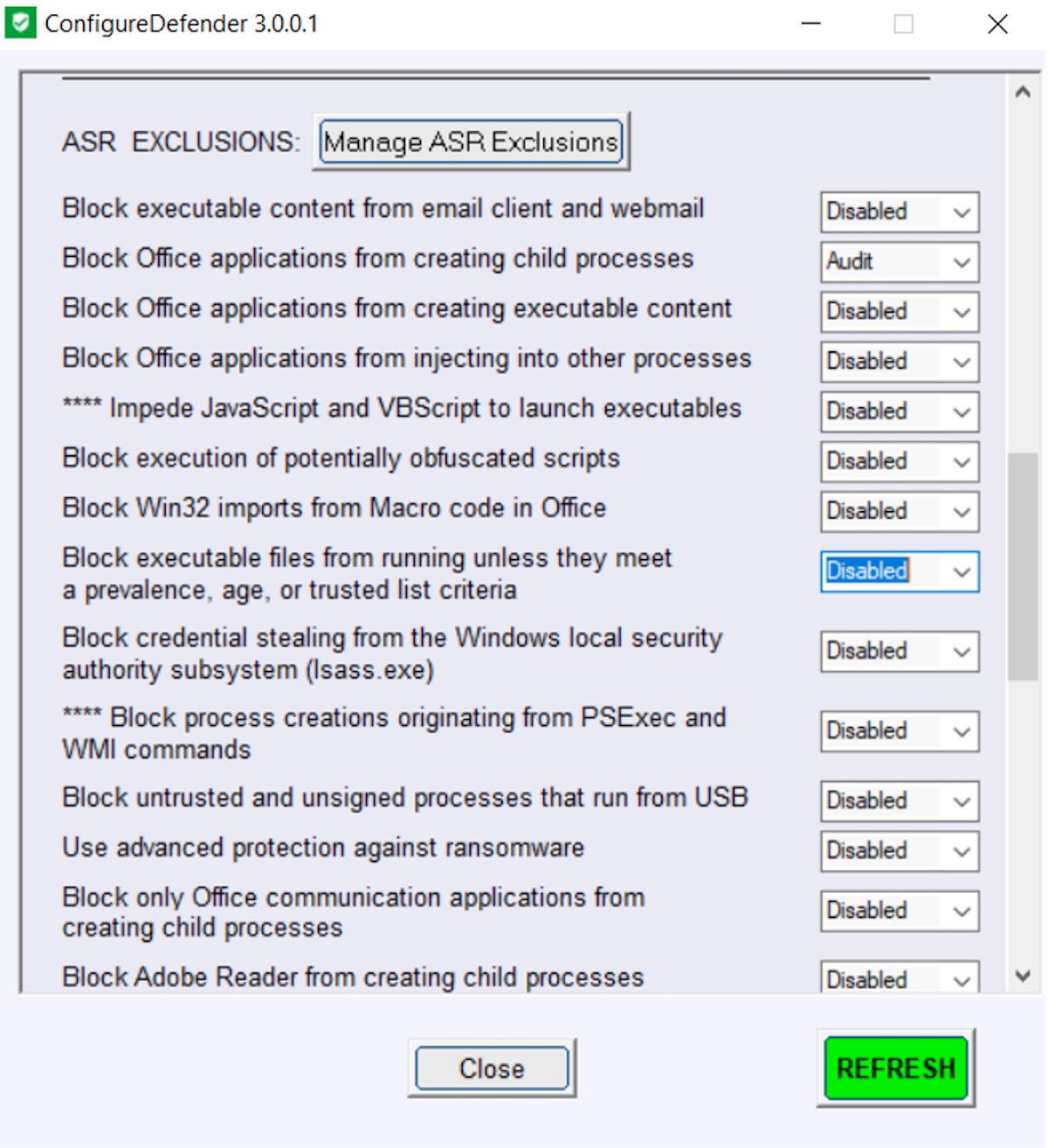 ConfigureDefender
ConfigureDefender The ConfigureDefender tool.
As noted on the ConfigureDefender site, different versions of Windows 10 provide different tools for Defender. All Windows 10 versions include Real-time Monitoring; Behavior Monitoring; scans of all downloaded files and attachments; Reporting Level (MAPS membership level); Average CPU Load while scanning; Automatic Sample Submission; Potentially unwanted application checks (called PUA Protection); a base Cloud Protection Level (Default); and a base Cloud Check Time Limit. With the release of Windows 10 1607, the "block at first sight" setting was introduced. With version 1703, more granular tiers of Cloud Protection Level and Cloud Check Time Limit were added. And starting with 1709, Attack Surface Reduction, Cloud Protection Level (with extended Levels for Windows Pro and Enterprise), Controlled Folder Access and Network Protection showed up.
As you scroll through the tool, you'll notice a section that covers control for Microsoft's Attack Surface Reduction (ASR) rules. You'll also note that many of them are disabled. These are among the most overlooked settings in Microsoft Defender. While you will need an Enterprise license to fully expose monitoring across your network, even standalone computers and small businesses can take advantage of these settings and protections. As noted in a recent document, Microsoft Defender Attack Surface Reduction recommendations, there are several settings that should be safe for most environments.
The recommended settings to enable include:
- Block untrusted and unsigned processes that run from USB.
- Block Adobe Reader from creating child processes.
- Block executable content from email client and webmail.
- Block JavaScript or VBScript from launching downloaded executable content.
- Block credential stealing from the Windows local security authority subsystem (lsass.exe).
- Block Office applications from creating executable content.
Turning these settings "on" — meaning they block the action — usually won't adversely impact even standalone computers. You can use the tool to set these values and review any impact on your system. Most likely you won't even realize they're better protecting you.
Next, there are settings that should be reviewed for your environment to ensure they don't interfere with your business or computing needs. These settings are:
- Block Office applications from injecting code into other processes.
- Block Win32 API calls from Office Macros.
- Block all Office applications from creating child processes.
- Block execution of potentially obfuscated scripts.
In particular, in an environment that includes Outlook and Teams a great number of events were registered if the setting of "Block all office applications from creating child processes" was turned on. Again, you can try these and see if you are affected.
The settings to watch out for include these:
- Block executable files from running unless they meet a prevalence, age, or trusted list criterion.
- Use advanced protection against ransomware.
- Block process creations originating from PSExec and WMI-commands.
- Block all Office communication applications from creating child processes.
These settings should be reviewed to make sure they don't hinder line-of-business apps and business processes. For example, while "Use advanced protection against ransomware" sounds like a setting everyone would want, in one business where a team had developed internal-use software, it created issues with developer workflows. (This setting specifically scans executable files entering the system to determine whether they are trustworthy. If the files resemble ransomware, this rule blocks them from running.)
The setting, "Block process creations originating from PSExec and WMI-commands," was especially troublesome, according to the authors. Not only did the setting lead to a large number of events in the audit log, it is incompatible with Microsoft Endpoint Configuration Manager, as the configuration manager client needs WMI commands to function properly.
If you have not looked at the additional settings in Microsoft Defender, download the zip file from github, unzip it and run ConfigureDefender.exe to see how these settings might affect your computing. You might be surprised to find you can add a bit more protection with no impact to your computing experience.
Copyright © 2021 IDG Communications, Inc.
Bedroom Set With Hidden Compartments
Source: https://www.computerworld.com/article/3604651/decoding-windows-defender-s-hidden-settings.html








Tidak ada komentar:
Posting Komentar